Summary
You are a cybersecurity analyst working in the Security Operations Center (SOC) of BookWorld, an expansive online bookstore renowned for its vast selection of literature. BookWorld prides itself on providing a seamless and secure shopping experience for book enthusiasts around the globe. Recently, you’ve been tasked with reinforcing the company’s cybersecurity posture, monitoring network traffic, and ensuring that the digital environment remains safe from threats.
Late one evening, an automated alert is triggered by an unusual spike in database queries and server resource usage, indicating potential malicious activity. This anomaly raises concerns about the integrity of BookWorld’s customer data and internal systems, prompting an immediate and thorough investigation.
As the lead analyst on this case, you are required to analyze the network traffic to uncover the nature of the suspicious activity. Your objectives include identifying the attack vector, assessing the scope of any potential data breach, and determining if the attacker gained further access to BookWorld’s internal systems.
Q1 - By knowing the attacker’s IP, we can analyze all logs and actions related to that IP and determine the extent of the attack, the duration of the attack, and the techniques used. Can you provide the attacker’s IP?
As I was going through the PCAP file, I saw a lot of communication between our Web server and a certain attacker attempting SQLi on our web server such as this one (packet 426):
| |
The IP of this attacker is the one below :
- 111.224.250.131
Q2 - If the geographical origin of an IP address is known to be from a region that has no business or expected traffic with our network, this can be an indicator of a targeted attack. Can you determine the origin city of the attacker?
Giving this IP address to ipinfo.io. We found the following information :
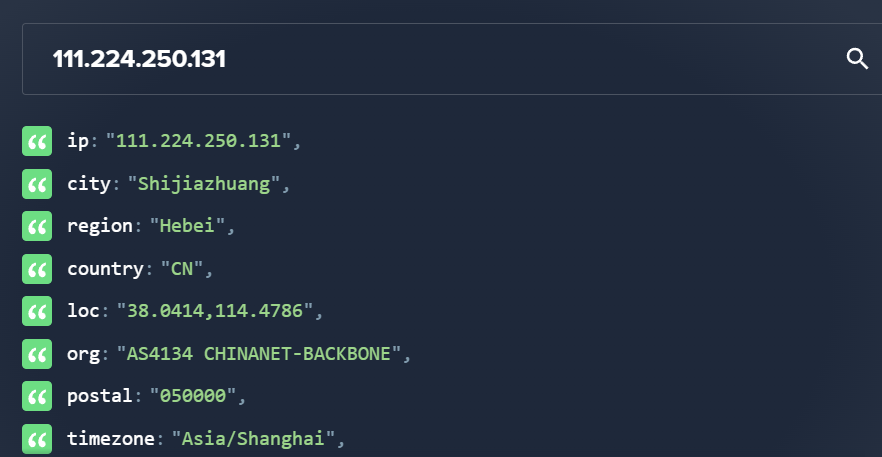
So it’s pretty straight forward that the answer we are looking for is Shijiazhuang
Q3 - Identifying the exploited script allows security teams to understand exactly which vulnerability was used in the attack. This knowledge is critical for finding the appropriate patch or workaround to close the security gap and prevent future exploitation. Can you provide the vulnerable script name?
Looking through the attacks, it seems that the search.php is vulnerable to multiple vulnerabilities such as SQLi and XSS.
Q4 - Establishing the timeline of an attack, starting from the initial exploitation attempt, What’s the complete request URI of the first SQLi attempt by the attacker?
The first SQLi attempted by the attacker is the one below. You can filter by time to match the attack timeline :
| |
Q5 - Can you provide the complete request URI that was used to read the web server available databases?
After analysis the following query (packet 1520) is the way that the attacker (actually sqlmap did) used to list the databases.
| |
Q6 - Assessing the impact of the breach and data access is crucial, including the potential harm to the organization’s reputation. What’s the table name containing the website users data?
Continuing the analysis we can find another SQLi listing table information (packet 1548) :
| |
The table containing user data is named customers. Here is a sample of extracted data :
| |
Q7 - The website directories hidden from the public could serve as an unauthorized access point or contain sensitive functionalities not intended for public access. Can you provide name of the directory discovered by the attacker?
Looking through the packets and filtering with the status code 200 (HTTP OK Reply). I found the admin directory (Packet 88699).
Q8 - Knowing which credentials were used allows us to determine the extent of account compromise. What’s the credentials used by the attacker for logging in?
Following the previous packet we can observe some credentials and a HTTP code 302
| |
We need to decode the password and we can found that the creds are the following admin:admin123!
Q9 - We need to determine if the attacker gained further access or control on our web server. What’s the name of the malicious script uploaded by the attacker?
With further analysis, we can notice a post request (Packet 88757) that the attacker has made to load his script on the system.
| |
It’s a simple reverse shell to the attacker IP address.
Conclusion
This challenge was quite easy (approx 1H for the challenge and writeup) but I give myself the challenge to do a writeup for every exercice so here I am :).