Summary
Our Intrusion Detection System (IDS) has raised an alert, indicating suspicious lateral movement activity involving the use of PsExec. To effectively respond to this incident, your role as a SOC Analyst is to analyze the captured network traffic stored in a PCAP file.
Q1 - In order to effectively trace the attacker’s activities within our network, can you determine the IP address of the machine where the attacker initially gained access?
At first glance, the attack seems to be originated from 10.0.0.133. On the packets below we can clearly see some attacks using SMB exploitation.
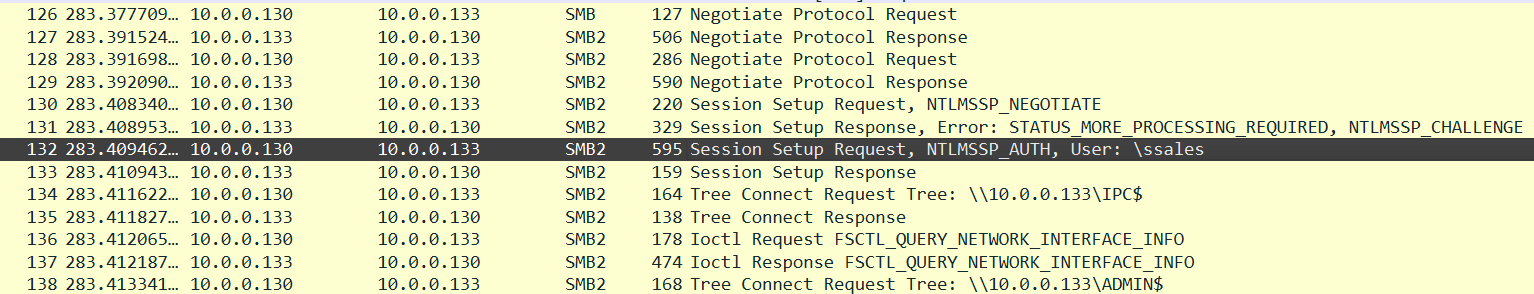
Response: 10.0.0.130
Q2 - To fully comprehend the extent of the breach, can you determine the machine’s hostname to which the attacker first pivoted?
As we can see in packet 132 and looking in the NTLMv2 Response, we have the machine’s hostname :
| |
Response: SALES-PC
Q3 - After identifying the initial entry point, it’s crucial to understand how far the attacker has moved laterally within our network. Knowing the username of the account the attacker used for authentication will give us insights into the extent of the breach. What is the username utilized by the attacker for authentication?
Parsing the different packets following the attack, we can observe a NTLMSSP. I found the following account used in the Session ID :
| |
Response: ssales
Q4 - After figuring out how the attacker moved within our network, we need to know what they did on the target machine. What’s the name of the service executable the attacker set up on the target?
The following packets (especially the 144) mentionned PSEXESVC.exe file which is the service for PSExec.
Response: PSEXESVC.exe
Q5 - We need to know how the attacker installed the service on the compromised machine to understand the attacker’s lateral movement tactics. This can help identify other affected systems. Which network share was used by PsExec to install the service on the target machine?
As seen in this packet in the tree id below :
| |
The network share used to install the service is ADMIN$.
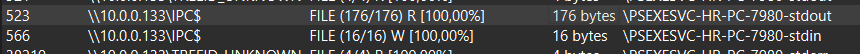
Q6 - We must identify the network share used to communicate between the two machines. Which network share did PsExec use for communication?
The net share used for PSExec communication is likely the IPC$ share as the Admin is only writeable and the attacker seems to redirect STDIN and STDOUT to IPC$. Images below :
Q7 - Now that we have a clearer picture of the attacker’s activities on the compromised machine, it’s important to identify any further lateral movement. What is the machine’s hostname to which the attacker attempted to pivot within our network?
Following the investigation on 10.0.0.130, we can see that the PSEXECSVC.exe file has been sent to 10.0.0.131 which match the hostname MARKETING-PC