Summary
The focus of this hands on lab will be an APT scenario and a ransomware scenario. You assume the persona of Alice Bluebird, the analyst who has recently been hired to protect and defend Wayne Enterprises against various forms of cyberattack.
In this scenario, reports of the below graphic come in from your user community when they visit the Wayne Enterprises website, and some of the reports reference “P01s0n1vy.” In case you are unaware, P01s0n1vy is an APT group that has targeted Wayne Enterprises. Your goal, as Alice, is to investigate the defacement, with an eye towards reconstructing the attack via the Lockheed Martin Kill Chain.
1. What is the name of the company that makes the software that you are using for this competition ? Just a six-letter word with no punctuation.
Answer :
| |
2. What is the likely IP address of someone from the Po1s0n1vy group scanning imreallynotbatman.com for web application vulnerabilities ?
Used Filter :
| |
Output :
| src_ip | count |
|---|---|
| 192.168.250.70 | 11493 |
| 23.22.63.114 | 2884 |
| 40.80.148.42 | 38416 |
This query return 3 results. 2 Public addresses and 1 private address. We can already eliminate the private one as it seems not to be an insider attack in the syllabus.
Time to search for headers !
Used Filter :
| |
We see some weird packets from 40.80.148[.]42 involving Acunetix Scanner. This seems to be what we searched for.
Packet example :
| src_ip | src_headers |
|---|---|
| 40.80.148.42 | CONNECT www.acunetix.wvs:443 HTTP/1.1 Host: imreallynotbatman.com Connection: Keep-alive Accept-Encoding: gzip,deflate User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.21 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.21 Acunetix-Product: WVS/10.0 (Acunetix Web Vulnerability Scanner - Free Edition) Acunetix-Scanning-agreement: Third Party Scanning PROHIBITED Acunetix-User-agreement: http://www.acunetix.com/wvs/disc.htm Accept: */* |
Response :
| |
3. What company created the web vulnerability scanner used by Po1s0n1vy ? Type the company name. (For example, “Microsoft” or “Oracle”)
Used Filter :
| |
Related to Q2.
Reponse :
| |
4. What content management system is imreallynotbatman.com likely using ? (Please do not include punctuation such as . , ! ? in your answer. We are looking for alpha characters only.)
Used Filter :
| |
A Content Management System (CMS) is used on our customer website. To find it, we are going to search for allowed action on the website during the vulnerability scan. Looking through the logs, we can see a lot of allowed action against “Joomla” CMS. After analysing all of these informations, it seems to be confirmed that the customer website use Joomla to manage its components.
Example :
| |
Response :
| |
5. What is the name of the file that defaced the imreallynotbatman.com website ? Please submit only the name of the file with the extension (For example, “notepad.exe” or “favicon.ico”).
Used Filter :
| |
When a site is defaced, it means that the original picture has been download by its server. In the filter above, we search for the filename downloaded by our webserver using a regex named fullname. Here is the output.
Output :
| fullname | count |
|---|---|
| com_joomlaupdate.xml | 1 |
| list.xml | 4 |
| poisonivy-is-coming-for-you-batman.jpeg | 3 |
| translationlist_3.xml | 1 |
Response :
| |
6. This attack used dynamic DNS to resolve to the malicious IP. What is the fully qualified domain name (FQDN) associated with this attack ?
Used Filter :
| |
Using what we used in the last question, we can filter with the full filename and get the site on which it was downloaded. In this case, it appears to be prankglassinebracket.jumpingcrab[.]com on port 1337
Response :
| |
7. What IP address has Po1s0n1vy tied to domains that are pre-staged to attack Wayne Enterprises ?
Looking for the domain in VirusTotal, we get the following IP address in the relations page 23.22.63.114
Response :
| |
8. Based on the data gathered from this attack and common open-source intelligence sources for domain names, what is the email address most likely associated with the Po1s0n1vy APT group ?
I was not very aware of good CTI platform, so I use Threatcrowd[.]com to find more information.
Beginning by the domain name : http://ci-www.threatcrowd.org/domain.php?domain=prankglassinebracket.jumpingcrab.com
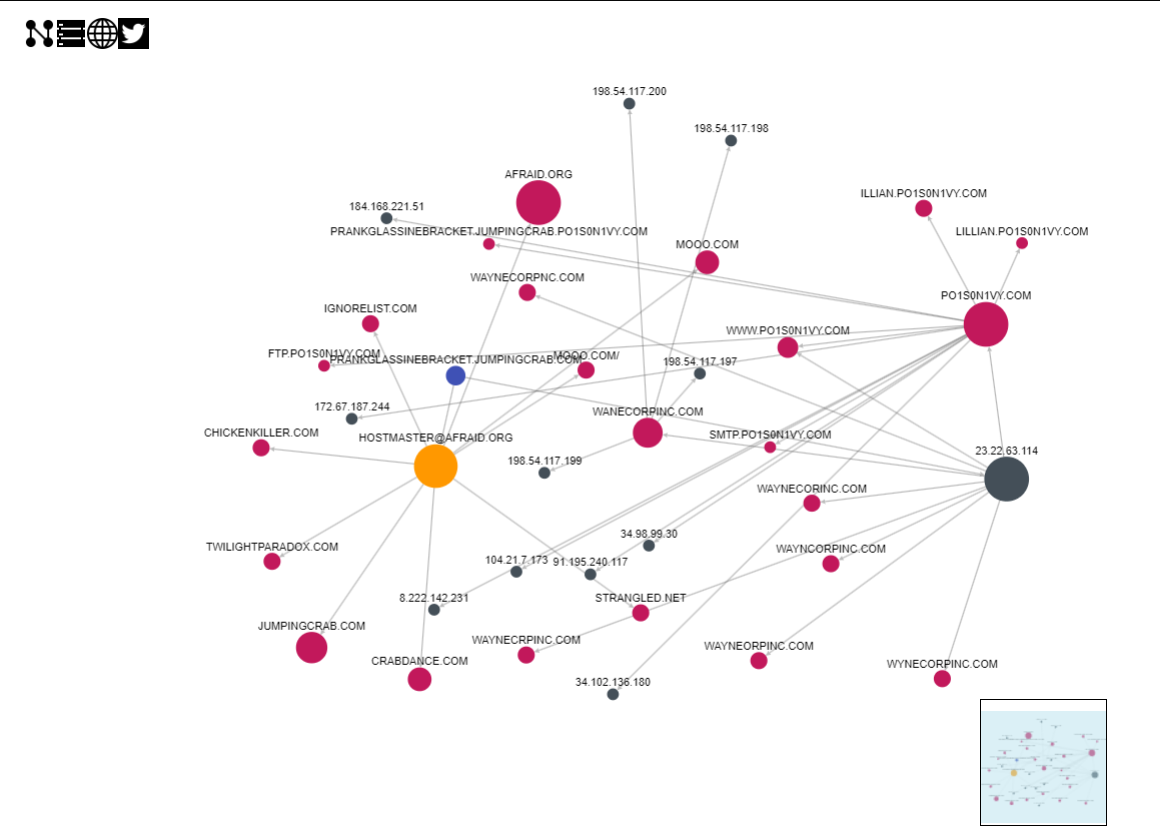
Looking through this map, I recognize the IP address 23.22.63.114 and pivot on this one with Alien Vault OTX. On this page (https://otx.alienvault.com/indicator/hostname/www.po1s0n1vy.com), I found the email address.
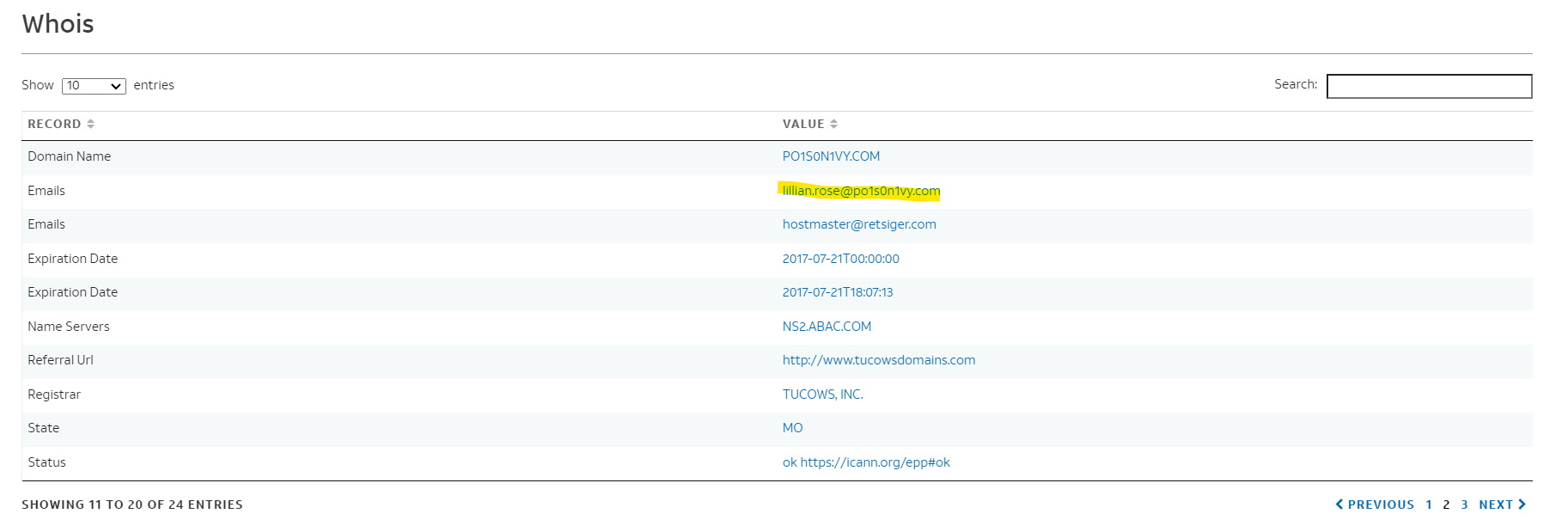
Response :
| |
9. What IP address is likely attempting a brute force password attack against imreallynotbatman.com ?
Used Filter :
| |
Back on Splunk, I have been searching for strange POST Method (as we are speaking about brute-force attack) and found that the IP of was doing some weird request :)
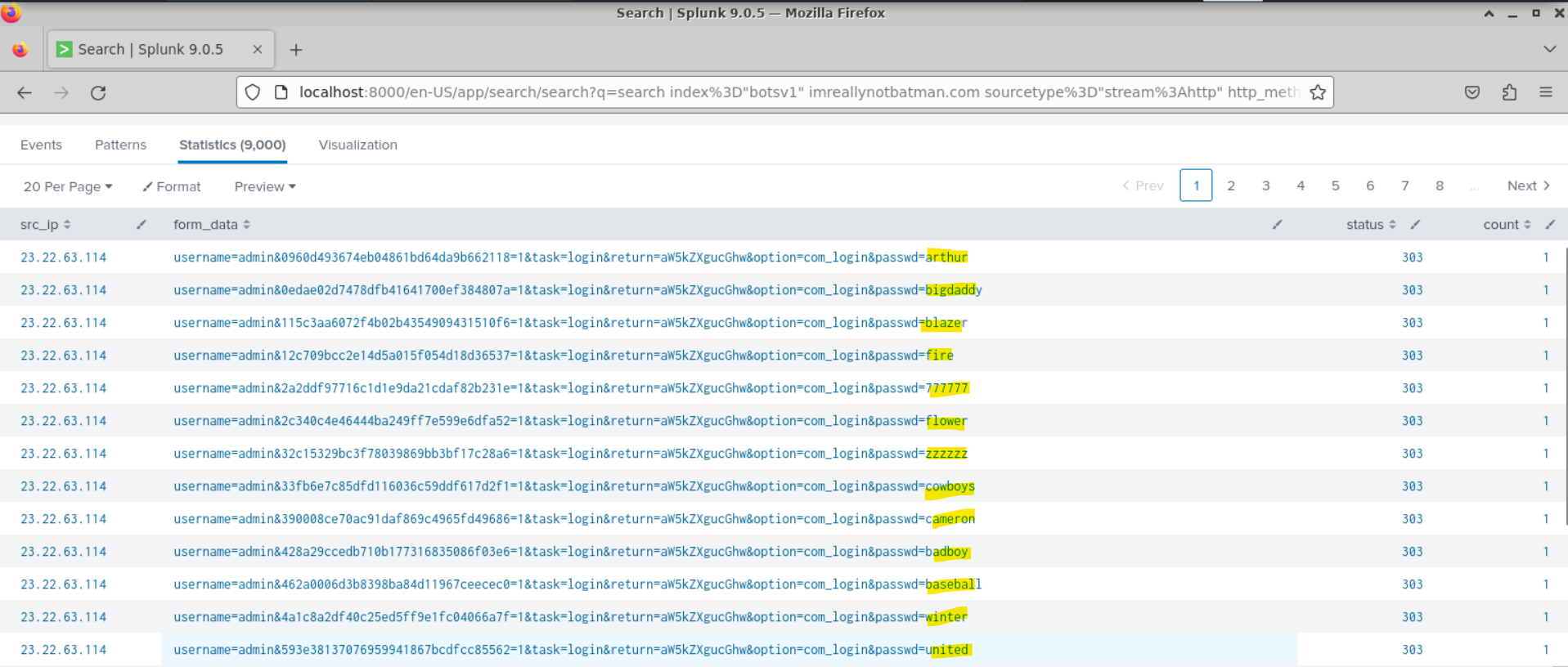
Response :
| |
10. What is the name of the executable uploaded by Po1s0n1vy ? Please include the file extension. (For example, “notepad.exe” or “favicon.ico”)
While I was looking through Joomla stream, I found some logs with filename uploaded by user:
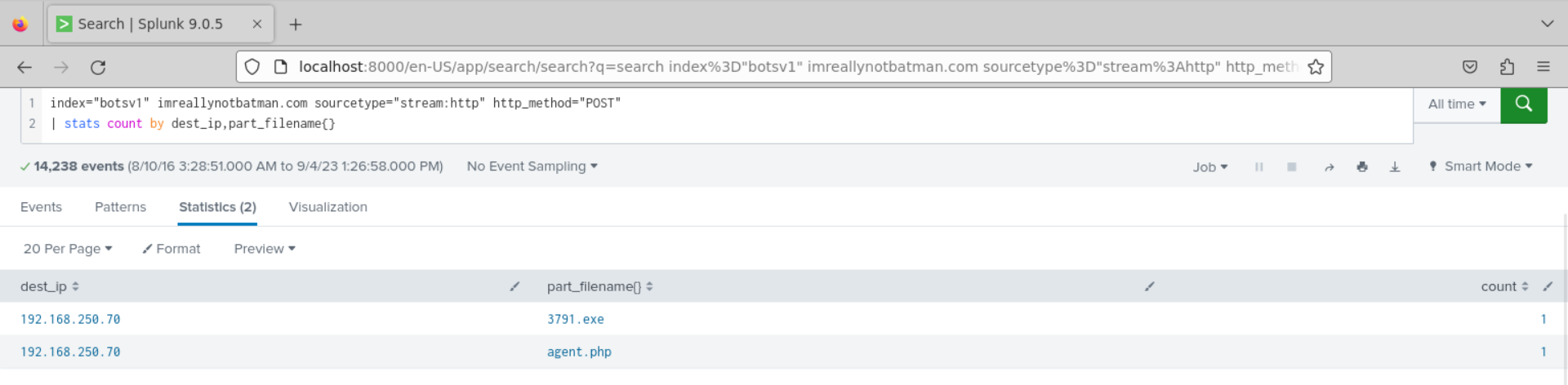
Used Filter :
| |
It may be the agent.php but looking through the the Content-Disposition field, I saw that the exe magic bytes appear in the raw data.
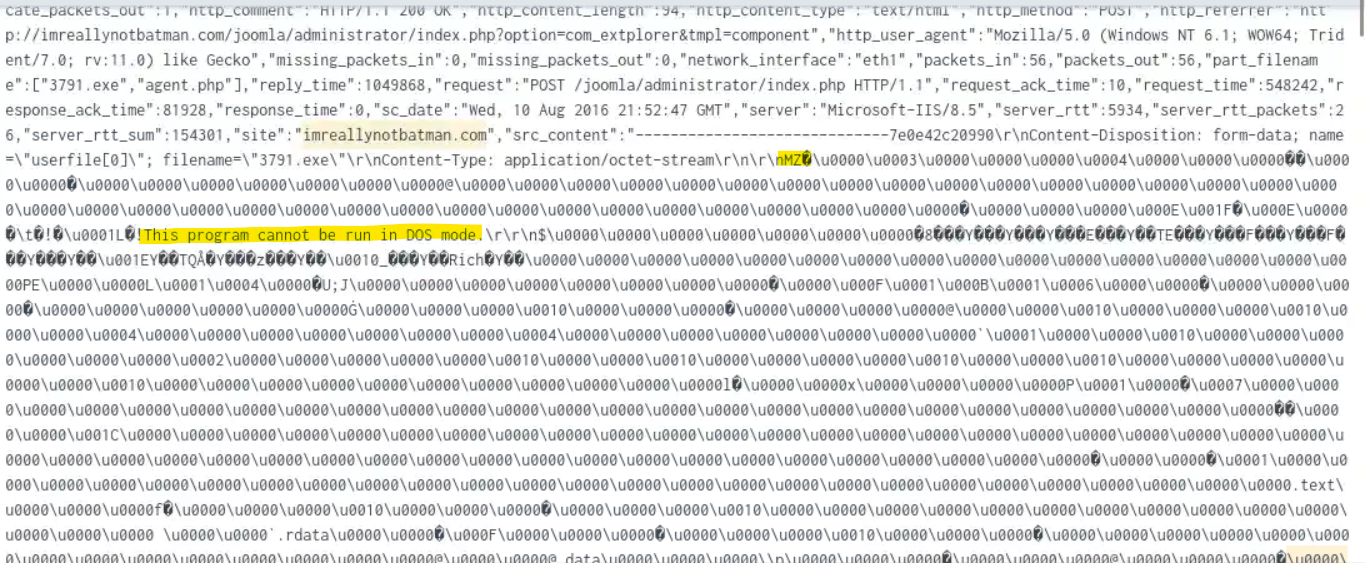
Response :
| |
11. What is the MD5 hash of the executable uploaded ?
Used Filter :
| |
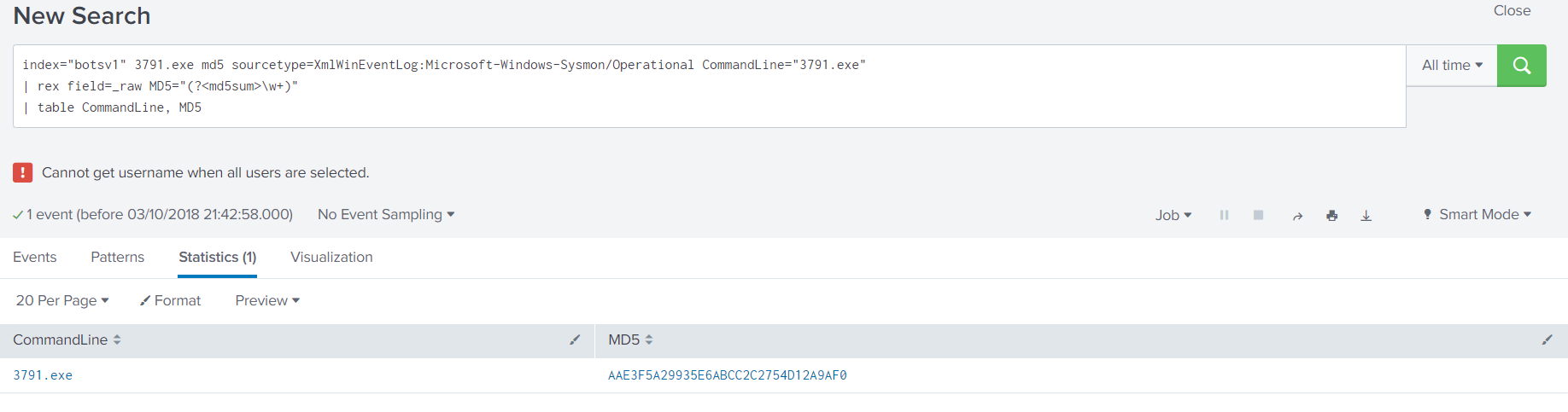
Looking on VT, we have something like this. Which seems pretty malicious : https://www.virustotal.com/gui/file/ec78c938d8453739ca2a370b9c275971ec46caf6e479de2b2d04e97cc47fa45d
Response :
| |
12. GCPD reported that common TTP (Tactics, Techniques, Procedures) for the Po1s0n1vy APT group, if initial compromise fails, is to send a spear-phishing email with custom malware attached to their intended target. This malware is usually connected to Po1s0n1vy’s initial attack infrastructure. Using research techniques, provide the SHA256 hash of this malware.
Looking on Virus Total with the APT Group’s IP Address, I found that there is four files communicating with this IP address :
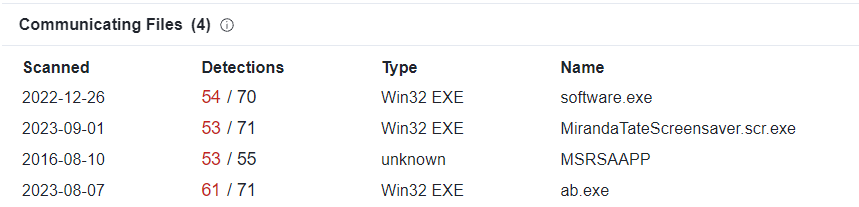
This file is the one we are looking for : https://www.virustotal.com/gui/file/9709473ab351387aab9e816eff3910b9f28a7a70202e250ed46dba8f820f34a8
Response:
| |
13. What is the special hex code associated with the customized malware discussed in question 12 ? (Hint: It’s not in Splunk)
In the community tab on the previous link, we found the hex code :
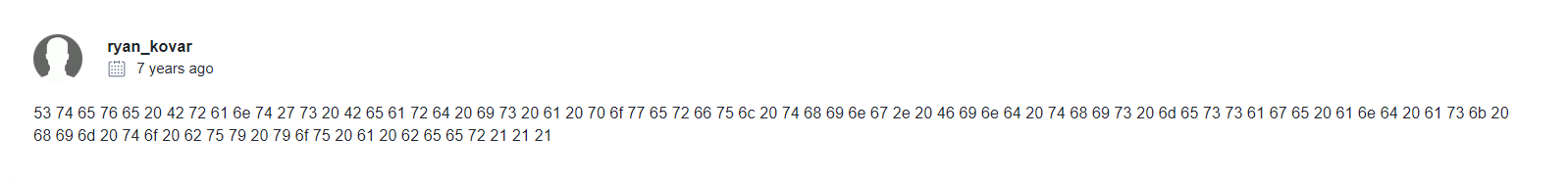
Response :
| |
14. One of Po1s0n1vy’s staged domains has some disjointed “unique” whois information. Concatenate the two codes together and submit them as a single answer.
Using https://www.whoxy.com/, I found the following information.
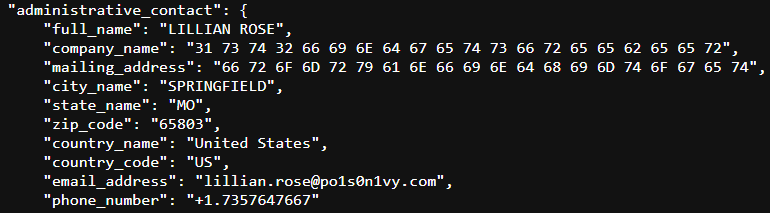
Response :
| |
15. What was the first brute force password used ?
Used Filter :
| |
On the Splunk interface, we can see the password attack sorted by time :
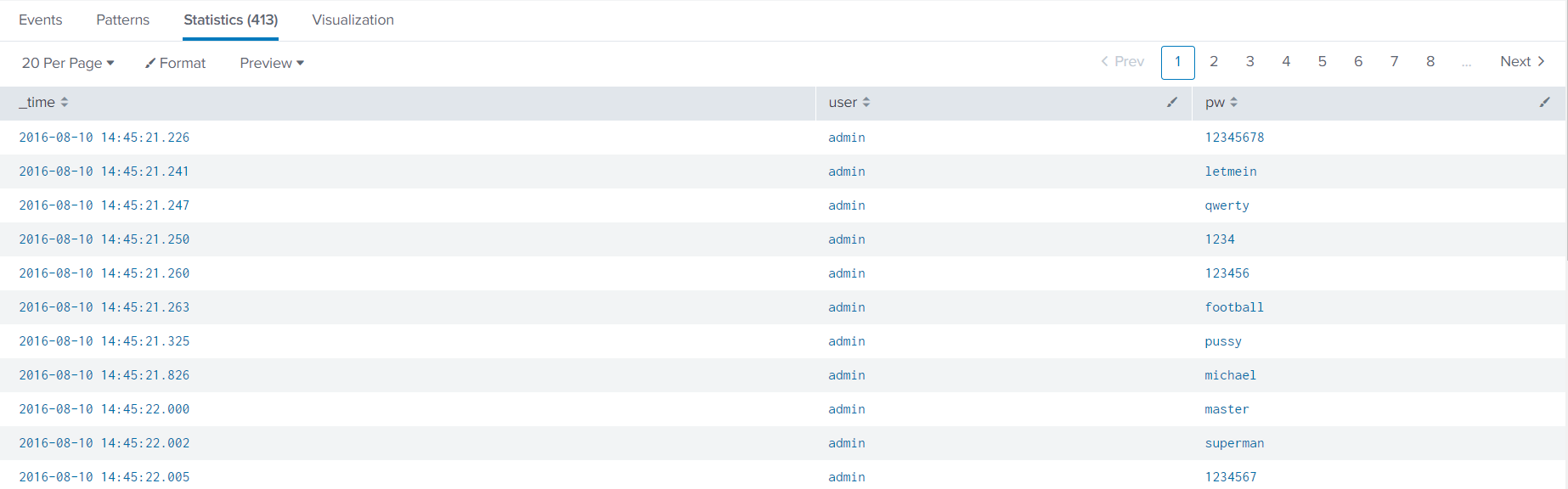
Response :
| |
16. One of the passwords in the brute force attack is James Brodsky’s favorite Coldplay song. Hint: we are looking for a six-character word on this one. Which is it ?
! TO-DO !
17. What was the correct password for admin access to the content management system running “imreallynotbatman.com” ?
Used Filter :
| |
Response :
| |
18. What was the average password length used in the password brute-forcing attempt ? (Round to a closest whole integer. For example “5” not “5.23213”)
Used Filter :
| |
Response :
| |
19. How many seconds elapsed between the brute force password scan identified the correct password and the compromised login ? Round to 2 decimal places.
Used Filter :
| |
Response :
| |
20. How many unique passwords were attempted in the brute force attempt ?
Used Filter :
| |
Response :
| |
21. What was the most likely IP address of we8105desk in 24AUG2016 ?
Used filter :
| |
Response :
| |
22. Amongst the Suricata signatures that detected the Cerber malware, which one alerted the fewest number of times ? Submit ONLY the signature ID value as the answer. (No punctuation, just 7 integers.)
Used filter :
| |
Response :
| |
23. What fully qualified domain name (FQDN) makes the Cerber ransomware attempt to direct the user to at the end of its encryption phase ?
Used Filter :
| |
Response :
| |
24. What was the first suspicious domain visited by we8105desk in 24AUG2016 ?
Used Filter :
| |
Response :
| |
25. During the initial Cerber infection a VB script is run. The entire script from this execution, pre-pended by the name of the launching .exe, can be found in a field in Splunk. What is the length in characters of the value of this field ?
Used Filter :
| |
Response :
| |
26. What is the name of the USB key inserted by Bob Smith ?
| |
Response :
| |
27. Bob Smith’s workstation (we8105desk) was connected to a file server during the ransomware outbreak. What is the IP address of the file server ?
Used Filter :
| |
Response :
| |
28. How many distinct PDFs did the ransomware encrypt on the remote file server ?
Used Filter :
| |
Response :
| |
29. The VBScript found in question 25 launches 121214.tmp. What is the ParentProcessId of this initial launch ?
Used Filter :
| |
Response :
| |
30. The Cerber ransomware encrypts files located in Bob Smith’s Windows profile. How many .txt files does it encrypt ?
| |
Response :
| |
31. The malware downloads a file that contains the Cerber ransomware crypto code. What is the name of that file ?
Used Filter :
| |
Response :
| |
32. Now that you know the name of the ransomware’s encryptor file, what obfuscation technique does it likely use ?
Used Filter :
| |
Response :
| |